
Urgent Need for Vulnerability Management in Government Organisations

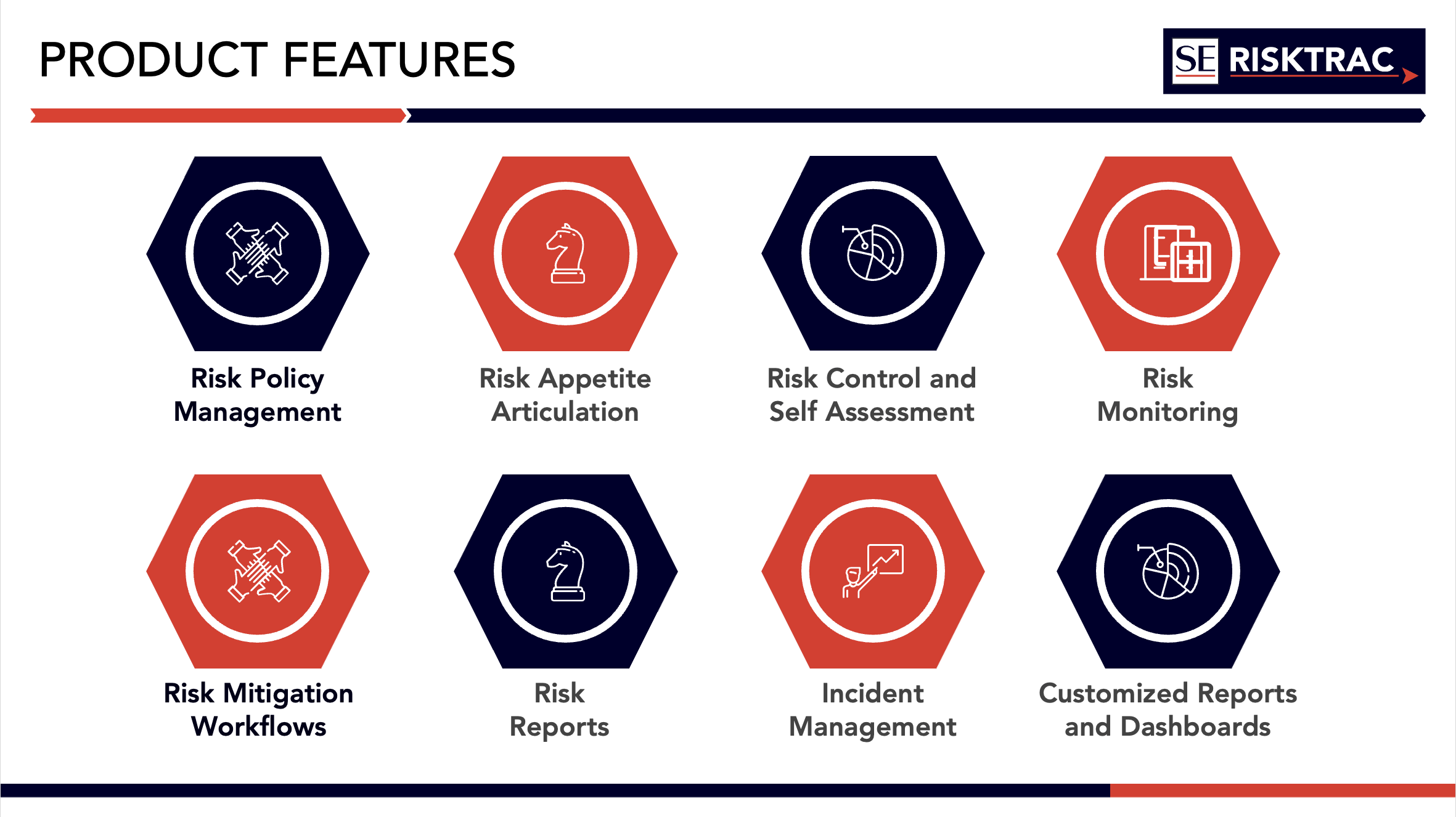
SE-RISKTRAC is a comprehensive solution that digitizes your Operational Risk Management (ORM) and Business Continuity Management (BCM) processes.
From identifying and assessing risks to monitoring and mitigating them, SE-RISKTRAC enables organizations to achieve operational excellence by addressing risks arising from people, processes, systems, or external events.
Digital relationships with third-party providers increase opportunities for growth, but they also increase opportunities for cyberattacks. Third-Party Risk Management (TPRM) is the process of analyzing and controlling risks presented to your organization by outsourcing to third-party vendors (TPV). Monitoring of the TPV compliance status helps to provide the organization with assurance and awareness about whether the vendor is complying with the applicable requirements for the services provided.
Unified Risk Visibility: Gain a holistic view of risks across your organization with seamless integration of KRIs, RCSAs, and incident reporting.
Data-Driven Decisions: Access real-time insights to make informed decisions that mitigate risks and enhance control strategies.
Operational Excellence: Minimize losses and improve efficiency by proactively identifying and addressing operational risks.
Collaboration Simplified: Break silos with a unified platform that connects departments and streamlines communication.
Scalable: Tailored for organizations of all sizes and industries.
Intuitive Interface: Easy-to-use workflows and dashboards for effective adoption.
Seamless Integration: Works effortlessly with your existing systems and processes.
Expert Support: Backed by SecurEyes’ 18+ years of cybersecurity excellence.
Digital relationships with third-party providers increase opportunities for growth, but they also increase opportunities for cyberattacks. Third-Party Risk Management (TPRM) is the process of analyzing and controlling risks presented to your organization by outsourcing to third-party vendors (TPV). Monitoring of the TPV compliance status helps to provide the organization with assurance and awareness about whether the vendor is complying with the applicable requirements for the services provided.
Multiple auditing programs from various departments can be incorporated into the system.

Integrating data from different sources to track and manage vulnerability in real time.

Monitoring and tracking the vulnerabilities that have been allocated to various organizational departments.
Safely exchanging remediation, evidence, data, and information across all organizational departments.

Providing a platform to digitize the inspection lifecycle.

Providing the tracking team with complete visibility into what's ahead, allowing you to assess the maximum vulnerability in the least amount of time.

Securely uploading remediated vulnerabilities for future reference.

Demonstrating how vulnerabilities are controlled through a drill-down dashboard that provides real-time reports and actionable insights.

Mapping uploaded vulnerabilities immediately to various regulatory frameworks.
Key Risk Indicators (KRIs):
Incident Management:
Risk Control Self-Assessment (RCSA):
Risk Appetite Framework:
Reduce Risk-Related Losses:
Save Time and Costs:
Boost Confidence:
Achieve Compliance Effortlessly:

Healthcare

Logistics

Retail

Aviation

Technology

Insurance

Banking

Telecom



I was really happy with the way the project went. It was a pleasure working with you guys. Your processes and documentations are excellent.
Founding Member of OWASP and Consulting Directory, Foundstone Inc.
It was a great pleasure to work with you and your team. The support, performance, and professionalism you showed assured ANB that doing business with SecurEyes was the right choice. I look forward to working with you on future projects.
CISO, Arab National Bank (ANB)
Thank you so much for your usual support and cooperation. Your continuous valuable efforts are appreciated, and they increase our confidence that we chose the right trusted partner.
CISO, Saudi Investment Bank
SecurEyes have reviewed all applications and systems in AXA to Perform detailed User to Role Mapping & Role to Feature Mapping. The team also Perform risk assessment on these applications and reported their observations on key areas which needs improvements. Overall, we are very satisfied with the deliverables of the project also the consultants that worked with us were very professional and knowledgeable. I look forward to working with SecurEyes again.
Information Security Manager AXA Cooperative Insurance Company
SecurEyes was to design, develop, implement & maintain the ISMS ISO 27001:2013 within our business. They ensured full success in this project as well as other projects, which contributed to the success of the InfoSec Department. This was recognized by the CEO & executive management due to the professionalism, expertise and commitment that SecurEyes team had throughout the project. Value added by SecurEyes is always above & beyond expectations.
Chief Information Security Officer, SAIB

Urgent Need for Vulnerability Management in Government Organisations

The story of a Cybersecurity Vulnerability

Cyber-Prepared for 2025, Are You?